Simply Cyber (vol 45) – Escape Plans: Incident Response And Business Continuity
Does anyone else feel stuck in the Groundhog Day loop?
This year’s Groundhog Day—2/2/22—is palindromic, reading the same forwards and backwards[i] and is the first Twosday of the year. (The next one is 22 February 22, which does indeed fall on a Tuesday.) According to legend, it’s a pivotal day that portends the change of season: Will there be another six weeks of winter or not?
Meanwhile, according to the Oxford Dictionary, Groundhog Day is “a situation in which a series of unwelcome or tedious events appear to be recurring in exactly the same way.” In the eponymous 1993 movie, self-centered main character Phil Collins (Bill Murray) is destined to repeat the past because he has failed to learn from it.[ii]
It takes energy to avoid repeating past behaviors, so perhaps it’s time for a resolution to create escape plans. A quick look at this month’s news stories suggests that we still have a lot to learn about cybersecurity health practices:
Lawsuit filed against Google during National Privacy Week. According to the filing 24 January by the states of Washington, Texas, Indiana—and the District of Columbia—Google has falsely represented its practices with respect to user location tracking, even when it appears as though tracking has been successfully disabled.[iii]
New “wiper ransomware” variant: WhisperGate. This malware, which hit multiple Ukrainian government websites, “bricks” (renders unusable) a compromised device so that recovery is not possible, even after paying the bitcoin ransom demanded.[iv] Does this portend a repeat of the December 2015 cyberattacks on the Ukraine power grid?
Patches for vulnerabilities in macOS Catalina and iOS. Apple sent an urgent update January 26 to fix documented security flaws, including zero-day exploits.[v]
Persistently lame passwords. The following list shows the top 10 most commonly used passwords in 2021. It’s based on analysis of 15,212,645,925 passwords, of which 2,217,015,490 were unique.[vi]
123456
123456789
qwerty
password
12345
qwerty123
1q2w3e
12345678
111111
1234567890
Cybersecurity Escape Plans for 2022
- Strengthen your personal password strategy. Really.
- Use as a tool to determine whether your passwords are sufficiently strong (or already compromised).
- Consider using a password management tool if that’s more your style.
- Implement multifactor authentication (MFA) for all the accounts and information that you care about.
- Never agree that a browser, website, or program remember your password.
- Back up valuable information to three locations: computing device, cloud, external hard drive. Recovery of lost information is uncertain and expensive. (I know; I’ve paid the price.)
- Develop an incident response plan. Although preventing a zero-day or advanced persistent threat attack may be an unrealistic objective, limiting the impact of successful attack is not. The manufacturing companies with which I work say that upstream clients request incident response plans more frequently than in the past. They are seeking assurance that their suppliers can perform. Ideally, the incident response plan (IRP) should extend to comprehensive consideration of business continuity planning (BCP). This requires a holistic look at organizational priorities and determination of which system is critical to survival:
- What systems are in place? (NOTE: A range of systems should be considered including power, HVAC, communications, shop floor, digital/paper records.)
- How critical is the system?
- What is the functional impact of a system failure?
- What is the business impact of a system failure?
- What is the recoverability impact of a system failure?
- What is the probability of a system failure?
- How will our stakeholders be affected—and how will communications be handled?
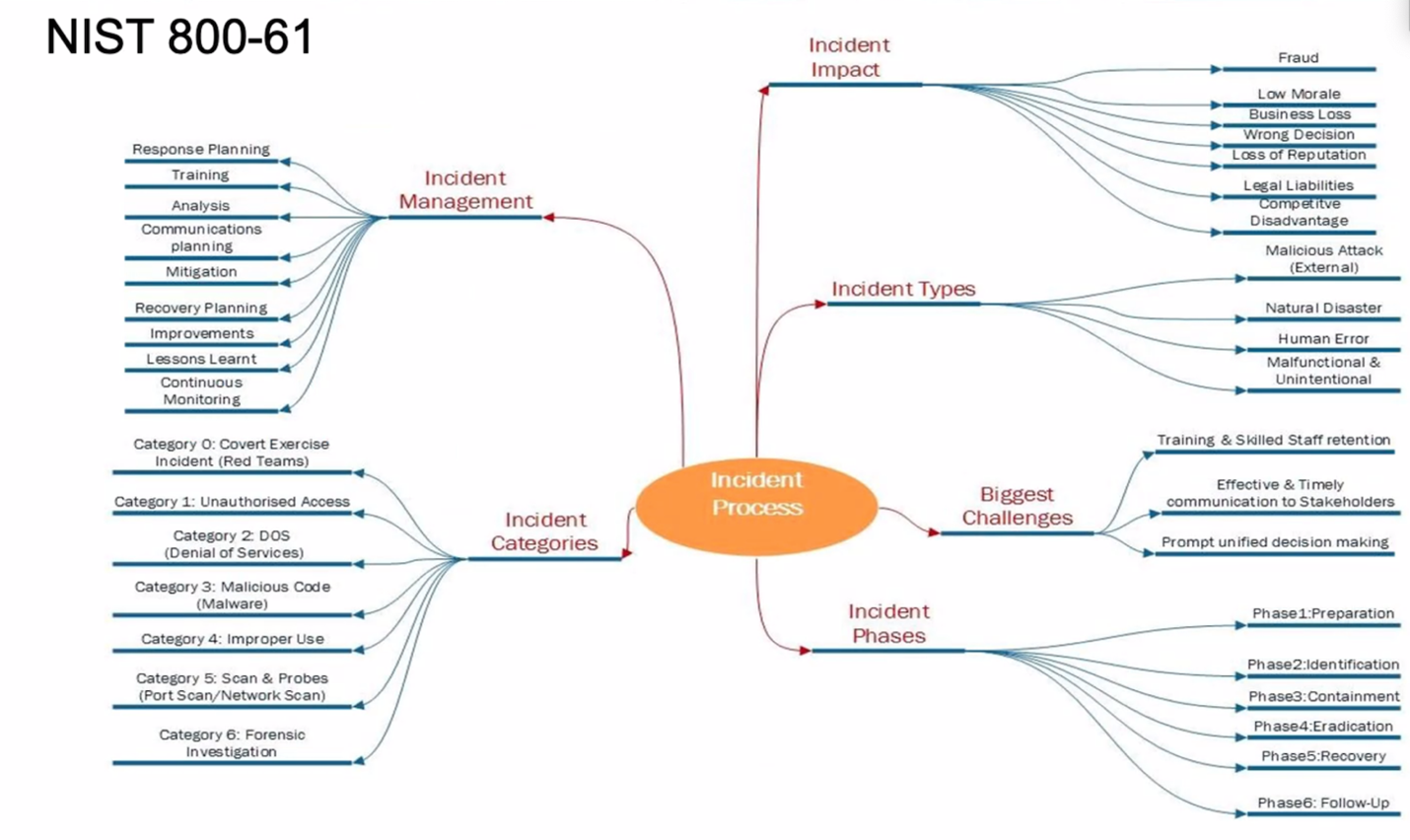
NIST SP 800-61r2 outlines a process for developing a computer incident response plan. The steps recommended can also be readily adapted to guide development of a business continuity plan. Convening a cross-departmental group for a tabletop exercise to test the plan for gaps is essential. Such exercises are typically structured around most-likely scenarios. The reality is that attempts to identify all possible unfortunate situations are futile. Meanwhile, layering what-if scenarios to reflect cascading failure paths can help incident response team members learn to think more creatively and critically—and become alert to signals indicating that conditions are moving in the wrong direction.
The graphic below captures key elements of the incident planning process.[vii]
Power of Planning
The power of the plan is in its associated planning, testing, and communicating processes. Former President General Dwight D. Eisenhower famously observed that, “In preparing for battle I have always found that plans are useless, but planning is indispensable.”
In the movie, Groundhog Day, the main character finally plans to change his behavior after receiving repeated slaps in the face from the object of his desire (Rita, played by Andie MacDowell). Along the way, he becomes more conscious of others and becomes a better person. Now to start cataloguing my data files and backing up those that I really value . . . Good luck with your plans!
[i] I consider it a palindrome, even though 2 February 2022 did not make the University of Portland lists https://faculty.up.edu/ainan/palindromedates21stcentury2011.pdf.
[ii] To George Santayana, a Spanish philosopher, is attributed the adage: “Those who cannot remember the past are doomed to repeat it.”
[iii] https://techcrunch.com/2022/01/24/google-lawsuit-location-dc-privacy/
[iv] https://www.securityweek.com/ukraine-attack-hackers-had-access-months-causing-damage
[v] https://www.securityweek.com/apple-patches-actively-exploited-ios-security-flaw
[vi] https://cybernews.com/best-password-managers/most-common-passwords/
[vii] From CISA: https://fedvte.usalearning.gov/courses/FCRM/course/videos/pdf/FCRM_D04_S01_T02_STEP.pdf